How to Actually Disable Windows Defender
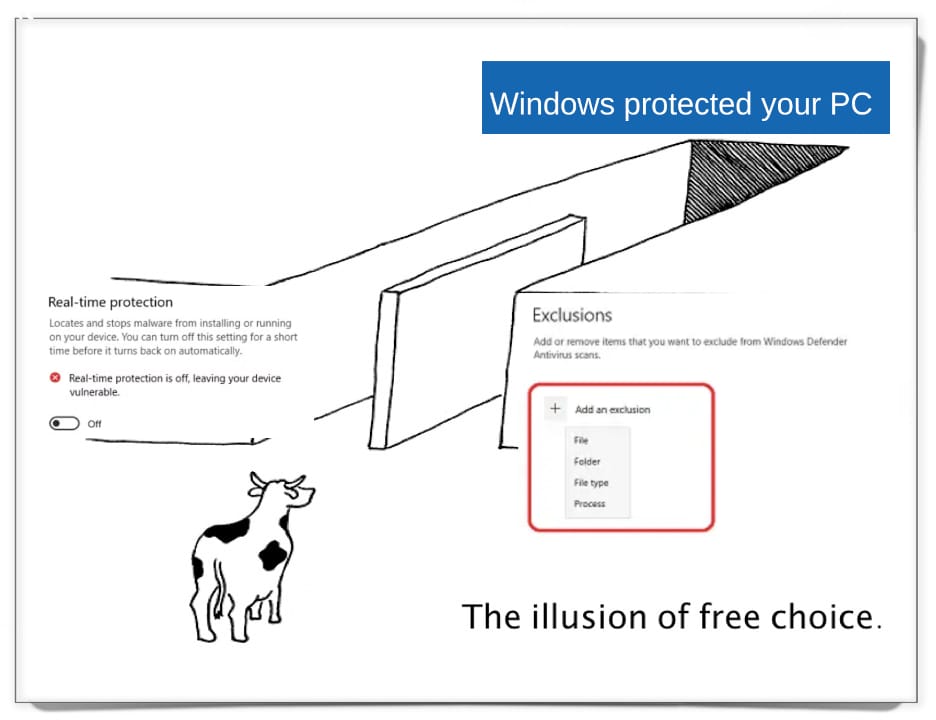
Article Purpose People starting out on their computer security journey can be put off from using Microsoft Windows because the OS ships with a persistent antivirius (which is actually quite robust). Disabling this AV is required to load any sort of unobfuscated hacking tools onto the OS, but simply “switching off” Windows Defender in the […]
The Next Step in Your Security Journey: Vulnerability Assessments

Previously, we discussed the process of creating a Threat Map to identify ways in which attackers may target your organization and what you can do to begin mitigating those threats. The next step in your security journey is to conduct a Vulnerability Assessment. This process is an essential part of all organizations’ overall risk management […]
Findings Series: Cross-Site Scripting (XSS)

Contents Description Classification Examples Remediation References Description Cross-site scripting (XSS) is a code injection attack caused by improper input sanitization of user input in web applications. Attackers submit malicious input to a web application and run JavaScript functions that can dump cookies, hijack sessions, or even log keystrokes from a victim’s browser. XSS vulnerabilities are […]
Findings Series: Weak Password Policy

Contents Description Classification Examples Remediation References Description Applications and environments are often only as secure as their weakest user account password. To prevent initial compromise from occurring through account takeover, it is common to enforce complexity, length, and renewal requirements for passwords across an application or network. When these requirements are not stringent enough (or […]
Findings Series: Deprecated TLS/SSL Protocol Versions Supported

Contents Description Classification Examples Remediation References Description Transport Layer Security (TLS) and Secure Socket Layer (SSL) Protocols are used to establish connections between a client and server. TLS/SSL protocols underlay a significant portion of the communcation conducted between computers. Vulnerabilites in TLS and SSL protocols arise from cryptographic failures often exploited throught an adversary-in-the-middle attack. […]
Business Email Compromise: Fortifying Your Business Against Email Deception

In today’s digital-first business world, one of the most subtle yet devastating weapons cyber adversaries employ is Business Email Compromise (BEC). It’s a sophisticated scam that preys not on the weaknesses in technology but on the trust within human relationships. BEC is an attack where a scammer uses compromised email accounts or spoofing techniques to […]
5 Practical Security Improvements For Small Businesses

Small businesses are increasingly becoming targets for cybercriminals. More often, attackers target smaller organizations because they’re perceived as easier targets with fewer resources dedicated to security. The good news is that improving your businesses cybersecurity doesn’t have to be complicated or expensive. Today, we’re discussing five practical security improvements that any small business can implement, […]
